Iso 27001 2013 Internal Audit Checklist Xls
Download this Iso 27001 Internal Audit Checklist if you want to comply with CyberSecurity Standards and control objectives. The purpose of compliance with IT security standards, such as Iso 27001, is to. Save Save iso-27001-compliance-checklist.xls For Later. 86% (29) 86% found this document useful (29 votes). ISO Compliance audit Checklist. ISMS Risk Assessment Manual v1.4. ISO 27001 Internal Audit Checklist.
If you are planning your ISO 27001 or ISO 22301 internal audit for the first time, you are probably puzzled by the complexity of the standard and what you should check out during the audit. So, you’re probably looking for some kind of a checklist to help you with this task. Here’s the bad news: there is no universal checklist that could fit your company needs perfectly, because every company is very different; but the good news is: you can develop such a customized checklist rather easily.
The steps in the internal audit
Let’s see which steps you need to take to create a checklist, and where they are used. By the way, these steps are applicable for internal audit of any management standard, e.g. ISO 9001, ISO 14001, etc.:
- Use an ISO 27001 audit checklist to assess updated processes and new controls implemented to determine other gaps that require corrective action. Internal audits and employee training Regular internal ISO 27001 audits.
- ISO 22301, privacy laws, PCI-DSS etc.). Annex A is merely a guide, a starting point. Design and implement an ISMS complying with all the mandatory elements specified in the main body of ISO/IEC 27001.
- This checklist is designed to streamline the ISO 27001 audit process, so you can perform first and second-party audits, whether for an ISMS implementation or for contractual or regulatory reasons. The checklist is intended as a generic guidance; it is not a replacement for ISO 27001.
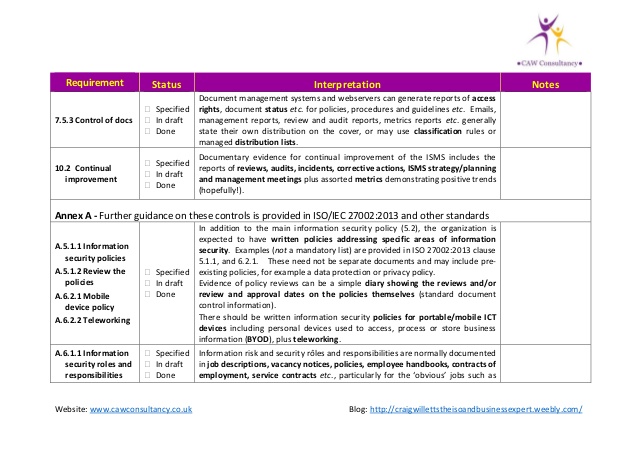
- Document review. In this step you have to read all the documentation of your Information Security Management System or Business Continuity Management System (or part of the ISMS/BCMS you are about to audit) in order to: (1) become acquainted with the processes in the ISMS, and (2) to find out if there are nonconformities in the documentation with regard to ISO 27001 or ISO 22301.
- Creating the checklist. Basically, you make a checklist in parallel to Document review – you read about the specific requirements written in the documentation (policies, procedures and plans), and write them down so that you can check them during the main audit. For instance, if the Backup policy requires the backup to be made every 6 hours, then you have to note this in your checklist, to remember later on to check if this was really done.
- Planning the main audit. Since there will be many things you need to check out, you should plan which departments and/or locations to visit and when – and your checklist will give you an idea on where to focus the most.
- Performing the main audit. The main audit, as opposed to document review, is very practical – you have to walk around the company and talk to employees, check the computers and other equipment, observe physical security, etc. A checklist is crucial in this process – if you have nothing to rely on, you can be certain that you will forget to check many important things; also, you need to take detailed notes on what you find.
- Reporting. Once you finish your main audit, you have to summarize all the nonconformities you found, and write an Internal audit report – of course, without the checklist and the detailed notes you won’t be able to write a precise report. Based on this report, you or someone else will have to open corrective actions according to the Corrective action procedure.
- Follow-up. In most cases, the internal auditor will be the one to check whether all the corrective actions raised during the internal audit are closed – again, your checklist and notes can be very useful here to remind you of the reasons why you raised a nonconformity in the first place. Only after the nonconformities are closed is the internal auditor’s job finished.
Making your checklist usable for beginners
So, developing your checklist will depend primarily on the specific requirements in your policies and procedures.
But if you are new in this ISO world, you might also add to your checklist some basic requirements of ISO 27001 or ISO 22301 so that you feel more comfortable when you start with your first audit. First of all, you have to get the standard itself; then, the technique is rather simple – you have to read the standard clause by clause and write the notes in your checklist on what to look for.
By the way, the standards are rather difficult to read – therefore, it would be most helpful if you could attend some kind of training, because this way you will learn about the standard in a most effective way. (Click here to see a list of ISO 27001 and ISO 22301 webinars.)
What to include in your checklist
Normally, the checklist for internal audit would contain 4 columns:
- Reference – e.g. clause number of the standard, or section number of a policy, etc.
- What to look for – this is where you write what it is you would be looking for during the main audit – whom to speak to, which questions to ask, which records to look for, which facilities to visit, which equipment to check, etc.
- Compliance – this column you fill in during the main audit, and this is where you conclude whether the company has complied with the requirement. In most cases this will be Yes or No, but sometimes it might be Not applicable.
- Findings – this is the column where you write down what you have found during the main audit – names of persons you spoke to, quotes of what they said, IDs and content of records you examined, description of facilities you visited, observations about the equipment you checked, etc.
Don’t be afraid
So, performing the internal audit is not that difficult – it is rather straightforward: you need to follow what is required in the standard and what is required in the ISMS/BCMS documentation, and find out whether the employees are complying with those rules.
If you have prepared your internal audit checklist properly, your task will certainly be a lot easier.
Learn how to perform an internal audit in this freeISO 27001 Internal Auditor Online Course.
If you enjoyed this article, subscribe for updates
Improve your knowledge with our free resources on ISO 27001/ISO 22301 standards.
Iso/iec 27001 Checklist
You may unsubscribe at any time.
For more information on what personal data we collect, why we need it, what we do with it, how long we keep it, and what are your rights, see this Privacy Notice.

Introduction
The ISO27k Toolkit is a collection of generic ISMS-related materials contributed by members of the ISO27k Forum, most of which are licensed under the Creative Commons. We are very grateful for the generosity and community-spirit of the donors in allowing us to share them with you, free of charge.
This is a work-in-progress: further contributions are most welcome, whether to fill-in gaps, offer constructive criticism, or provide additional examples of the items listed below.
Please observe the copyright notices and Terms of Use.
DISCLAIMER: these materials have been donated by individuals with differing backgrounds, competence and expertise, working for a variety of organizations in various contexts. They are models or templates, starting points if you will. Your information risks are unique, so it is incumbent on you to assess and treat your risks as you and your management see fit. Don’t blame us if the ISO27k Toolkit is unsuitable or inadequate for your circumstances: we are simply trying to help!
ISMS overview and introductory materials
- ISMS implementation and certification process flowchart v4.1 - a one-page outline of the entire process, contributed in English by Osama Salah and Gary Hinson. Also in Arabic and French thanks to Bachir Benyammi, German thanks to Markus Kähler and Hebrewthanks toTitans Security Academy
- ISMS implementation and certification overview presentation v2 contributed by Marty Carter.
- ISMS information risk management process flowchart describes the information risk management activities, contributed by Bachir Benyammi.
- List of ISO27k standards maintained by Gary Hinson.
- ISO27k FAQ contributed by members of the ISO27k Forum.
ISMS governance, management & implementation guidance
- ISMS implementation project estimator - a tool to estimate the timescale needed to implement an ISMS. Contributed by Gary Hinson, Ed Hodgson and Marty Carter.
- ISMS implementation plan - a skeleton or starter plan for you to expand and amend to suit your situation. Contributed by Marty Carter.
- ISMS implementation tracker - a combined status tracker for the mandatory ISMS and optional security controls in ISO/IEC 27001:2013, Statement of Applicability and Gap Analysis, used to track progress of the ISMS implementation project towards certification and beyond. Contributed by Ed Hodgson and team, in English and Spanish.
- ISMS mandatory documentation checklist - a detailed and explicit guide to the documentation and records formally required or recommended for certification against ISO/IEC 27001. Contributed by members of the ISO27k Forum.
- Generic ISO27k ISMS business case template v3 outlines the benefits and costs typically associated with an ISO27k ISMS for an investment or implementation project proposal or budget request. Contributed by Gary Hinson.
- ISO27k security awareness presentation v2 contributed by Mohan Kamat.
- Agenda for ISMS Management Review meeting based on inputs by Sean Malward, Richard Regalado and ISO/IEC 27001.
- ISO27k information security program maturity assessment tool contributed by EDUCAUSE Cybersecurity Program, the Higher Education Information Security Council and Bachir Benyammi
Model information security policies
- High level overall ISMS policy contributed by K. Faisal Javed.
- Change management and control policy contributed by a generous donor.
- Information classification policy contributed by Michael Muehlberger.
- Malware policy contributed by Gary Hinson.
- Outsourcing security policy contributed by Aaron D'Souza.
- Security awareness and training policy contributed by Gary Hinson.
ISMS procedures, guidelines and other supporting documents
- Corrective action procedure contributed by Richard Regalado.
- Corrective/preventive action record form contributed by Richard Regalado.
- Data restoration form contributed by Vladimir Prodan.
- FMEA risk analysis spreadsheet contributed by Bala Ramanan.
- GDPR-ISO27k mapping - since privacy, compliance, information risk and information security overlap, it makes sense to use an ISO27k ISMS to achieve and maintain compliance with the EU General Data Protection Regulation - contributed by the ISO27k Forum.
- Information asset inventory contributed by Steve McColl.
- Information classification matrix contributed by Richard Regalado.
- Information risk register v2 contributed by Madhukar.
- Information security controls cross-check spreadsheet in English, French and Spanish classifies controls from ISO/IEC 27002. Contributed & maintained by members of the ISO27k Forum.
- Introductory email introducing the ISMS implementation project and initial gap analysis/business impact analysis work to managers. Contributed by Marty Carter.
- ISMS auditing guideline v2created & maintained by members of the ISO27k Forum.
- ISMS internal audit procedure v3 contributed by Richard Regalado.
- Preventive action procedure contributed by Richard Regalado.
- Statement of Applicability (SoA) template - a team effort available in English, Spanish, German, French and Portuguese.
ISMS-related job descriptions/roles and responsibilities
- RASCI table v5 allocates roles and responsibilities associated with the security controls in ISO/IEC 27002, originally contributed by Matthias Wagner, now in English and French.
- Roles and responsibilities for contingency planning contributed by Gary Hinson and Larry Kowalski.
- Roles and responsibilities for information asset management contributed by Mohan Kamat.
Download the entire ISO27k Toolkit
Iso 27001 Internal Audit Template
Download the complete ISO27k Toolkit - a ZIP file containing most of the above materials.
That is version 2019-12 released in December 2019.
Terms and conditions of use
Please read and respect the copyright notices (if any) within the individual files.
Most items in the ISO27k Toolkit are released under the Creative Commons Attribution-Noncommercial-Share Alike license. You are welcome to reproduce, circulate, use and create derivative works from these materials provided that: (a) they are not sold or incorporated into commercial products, (b) they are properly attributed to the ISO27k Forum based here at ISO27001security.com, and (c) if they are published or shared, derivative works are shared under the same terms.

A few items belong to the individual authors or their employers. Please read the embedded copyright notices and, if necessary, contact the copyright holders directly for their permission to use or reproduce them. [They have of course given us permission to share them with you!]
Despite our best efforts, there are errors and omissions. The ISO27k Toolkit is a crowdsource community effort involving many people, most of whom are so busy that they can barely spare the time to get involved. Please don’t shoot the messenger! Help us identify and correct the errors, fill the gaps, fix broken links and generally improve the Toolkit for the benefit of the global community by emailing Gary@isect.com. Constructive feedback and additional content is especially welcome. Thank you.
Support this project
While this website, the ISO27k Toolkit and ISO27k Forum are provided entirely free of charge, there are substantial costs in providing these services. Aside from the costs involved in publishing and maintaining the website, we invest hundreds of hours per year in writing materials, responding to queries and so forth in conjunction with the ISO27k community. We are very grateful to the commercial sponsors who advertise on this site, and to those who contribute materials. If YOU value this service and want the project to continue, please click the ads to visit the sponsors’ websites. You never know, you might find exactly what you need right there, and you’ll be helping us keep this site going. Thank you too!
